Cybercriminals are constantly looking for new methods to defraud users, and previously unseen ones are beginning to proliferate.
Now ESET researchers have found Malware for Android can steal credit card data, use an NFC reader on an infected device and send the data to an attacker.
Basically it clones the card so that it can be used at ATMs or point of sale terminals.
This malware has been named as Engate Because it includes NFCGate, an open-source tool to capture, analyze or transform NFC traffic.
“This is a new attack scenario for Android, and the first time we've seen Android malware being used with this capability,” ESET researcher Lucas Stephanko said.
“The NGate malware can send NFC data from a victim's card through a compromised device to an attacker's smartphone, who can then emulate the card and withdraw money from an ATM.”
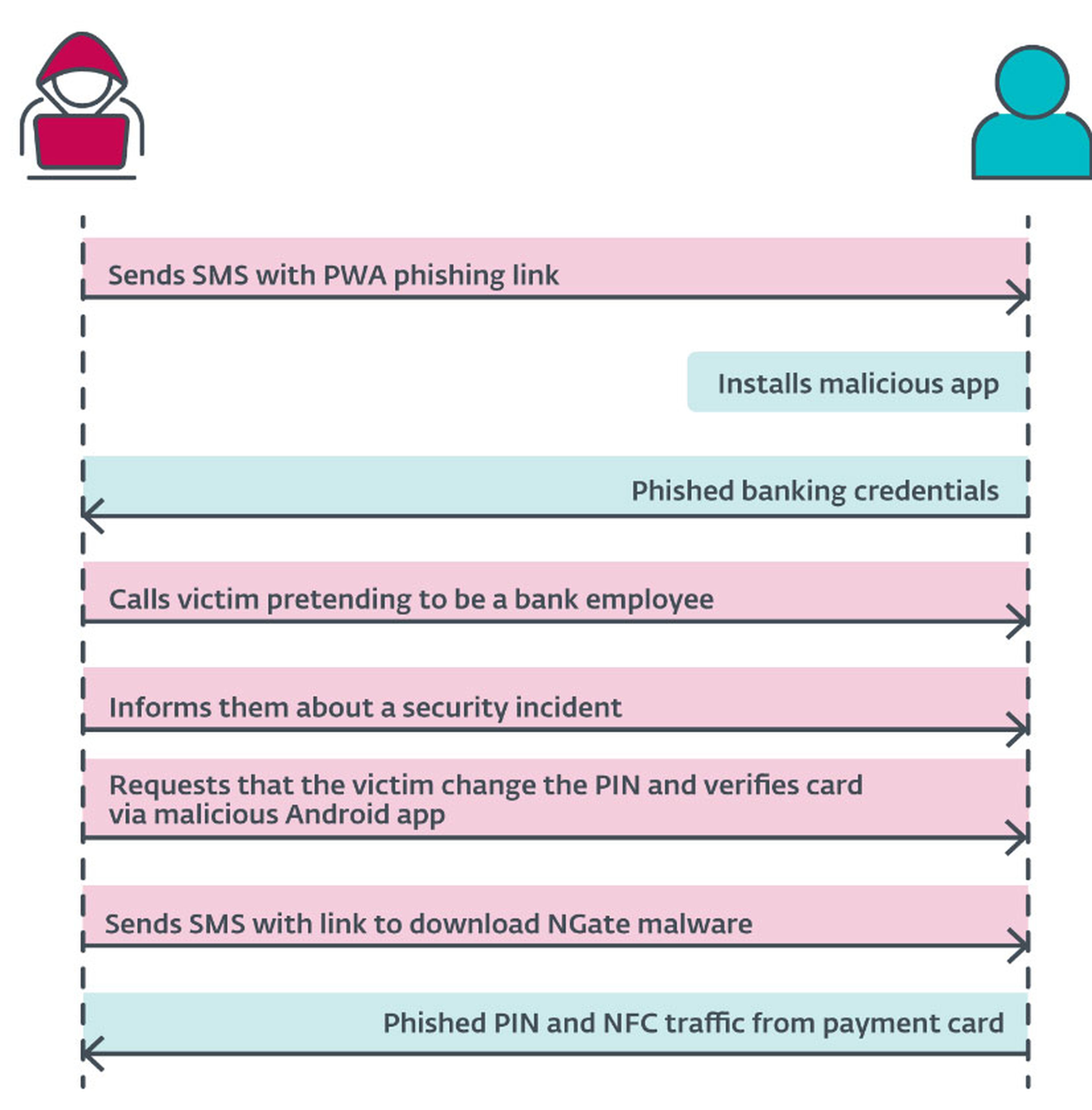
Malware May have been first installed through phishing campaigns Tricking victims into installing it from fraudulent domains posing as banks or official applications.
Some of these were issued in the form of applications Progressive Web Applications It can be installed on Android and iOS devices.
It seems that the person responsible for this scam was already arrested in March.
ESET
“The attack scenario began with attackers sending potential victims SMS messages about tax returns, which included a link to a phishing website posing as a bank. Often, these links led to malicious PWAs. Once the victim installed the app and entered their credentials, the attacker gained access to the victim's account. The person pretended to be a bank employee and told the victim that his account had been compromised, but this fact led to another lie.
“To “protect” their funds, the victim was asked to change their PIN and verify the bank card using a mobile app (NGate malware). A link to download NGate was sent via SMS. “In the NGate app, victims entered their old PIN to generate a new PIN, and to verify the change or use their We suspect the card will be placed on the back of the smartphone.”
“Since the attacker already had access to the compromised account, he could change the withdrawal limits. If the NFC relay method doesn't work, you can transfer the funds to another account. However, using NGate makes it easier for the attacker to access the victim's funds without leaving traces that lead to his own bank account,” he said. ESET explains.
Researchers point out These types of attacks can be used in other scenarios such as cloning some smart cards that are used for other purposes..
This cloning can occur in situations where an attacker has physical access to the card or can briefly read the card in purses, wallets, backpacks or cell phone cases.
Find out How we work Inside Computer Today.
Tags: Malware





:quality(85)/cloudfront-us-east-1.images.arcpublishing.com/infobae/KTKFKR763RBZ5BDQZJ36S5QUHM.jpg)